Solutions for
- Industries
- Commercial Companies
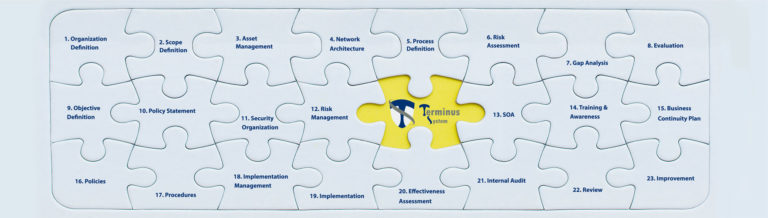
Our comprehensive and agile Information Security Management System model is designed to maximize organizational benefits while minimizing resource expenditure—including time, budget, and human effort. By strategically aligning the ISMS with your business objectives, it unlocks the full potential of your organization’s security.
Ultimate Security defines clear information security objectives, identifies key challenges and drivers, and provides a structured roadmap to assess, prepare, and successfully implement an effective ISMS.
Ultimate Security stands out by:
translating everyday business language into actionable security measures
This unique feature allows users to communicate their security needs in familiar terms, ensuring a seamless and stress-free experience. With Ultimate Security, achieving your security goals has never been easier.
Using this model, we examine the security status of the organization in the following areas:
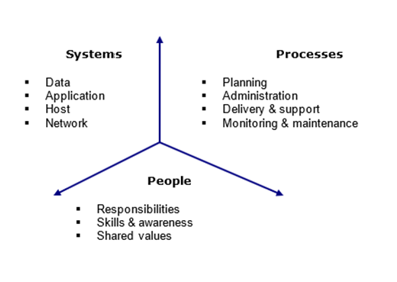
Our model helps organizations:
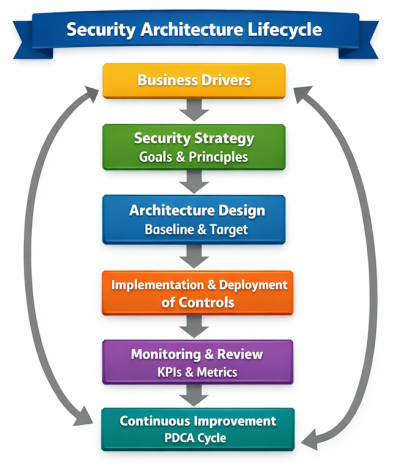
The methodology is characterized by four core features:
Following a cyclical improvement philosophy (Deming’s PDCA approach), ISMS implementation is iterative. Each cycle:
This approach ensures continuous enhancement of security aligned with evolving
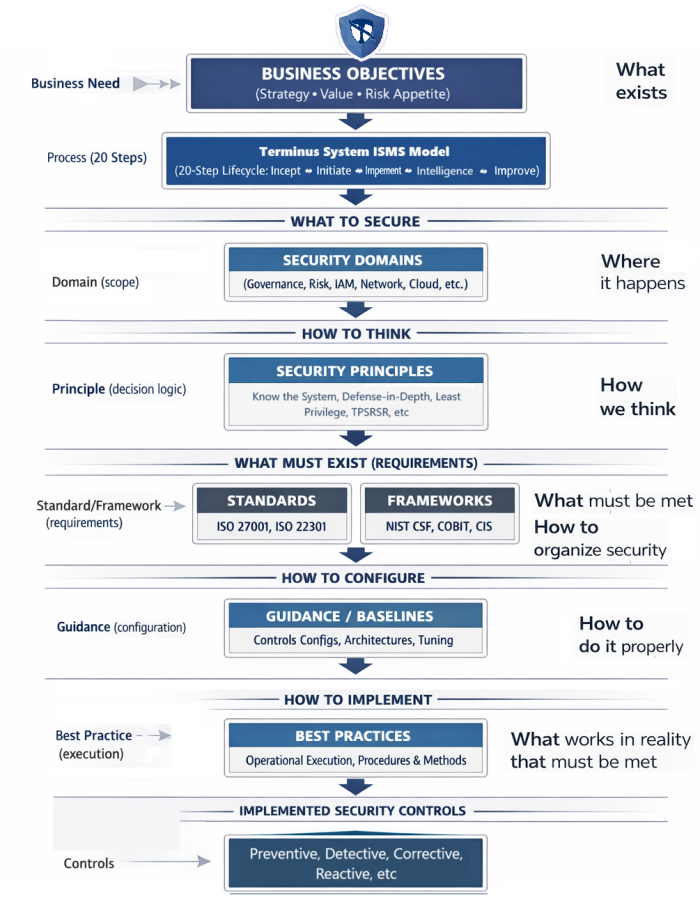
At the core of our methodology is a simple principle: protect your most valuable asset—data—while maximizing business value.
We consider all forms of data—digital, physical, and human knowledge—and address their full lifecycle:
Our approach is risk-driven and benefit-focused, applying the right controls to ensure confidentiality, integrity, and availability without overcomplicating implementation.
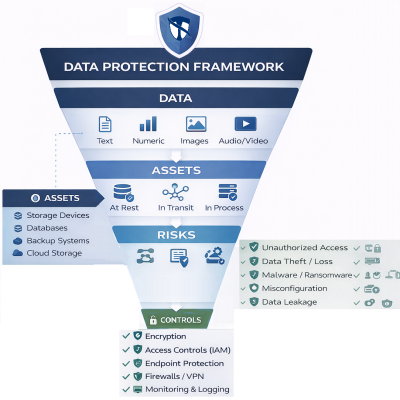
Why It Works:
How It’s Applied
Now, the important question is “What controls should we use for our case”?
To answer this question and design RTP (Risk Treatment Plan), this model is using all possible tools and facilities, including:
We integrate security domains, principles, frameworks, guidance, and best practices to create a tailored security program that is measurable, sustainable, and continuously improving.
Within Ultimate Security, security implementation follows a structured decision chain that transforms business intent into operational protection. Starting from the business need, the 20-step ISMS process defines a systematic path for implementation.
“Speak Business. Think Security.”
This process determines the appropriate security domains that define the scope of protection.
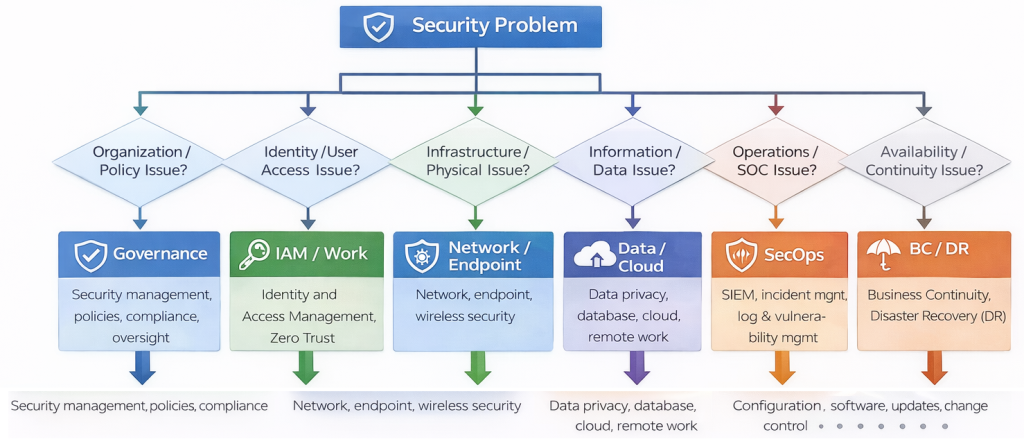
Each domain applies one or more security principles that provide decision logic and guide design choices. These principles and domains are then translated into formal standards and frameworks—such as ISO/IEC 27001 or NIST Cybersecurity Framework—which define required controls and compliance expectations. From these requirements, organizations derive guidance and baselines that specify technical configurations and architectural settings.
Each guidance baseline can generate multiple best practices that define operational procedures and execution methods, ultimately resulting in implemented security controls.
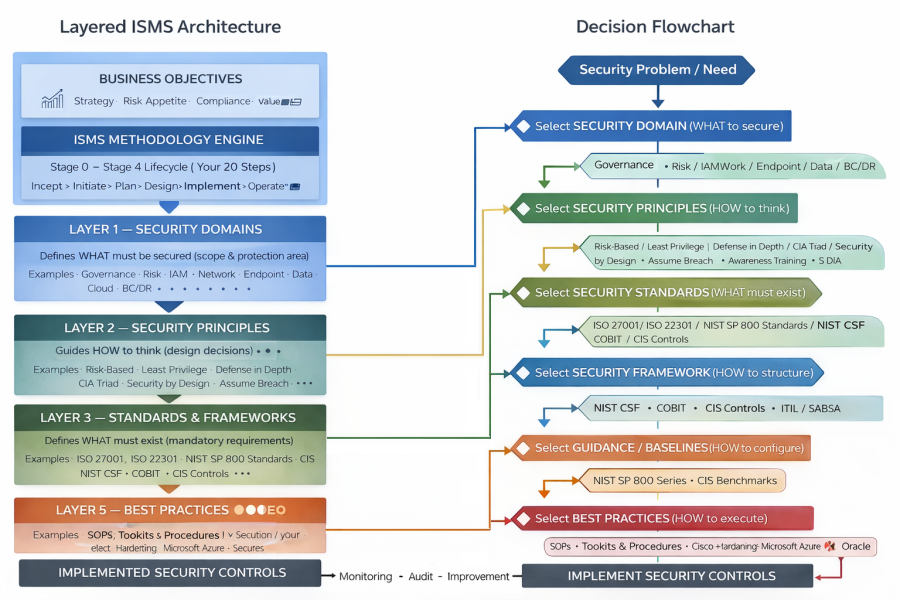
The relationships between these elements are dynamic and many-to-many: a single domain may relate to multiple principles and multiple frameworks or standards; one principle may map to several guidance or baseline configurations; a framework can also produce multiple guidance sources; and each guidance baseline may lead to several best practices.
This layered and interconnected structure ensures flexibility, consistency, and alignment between business objectives, risk management decisions, and practical security implementation.
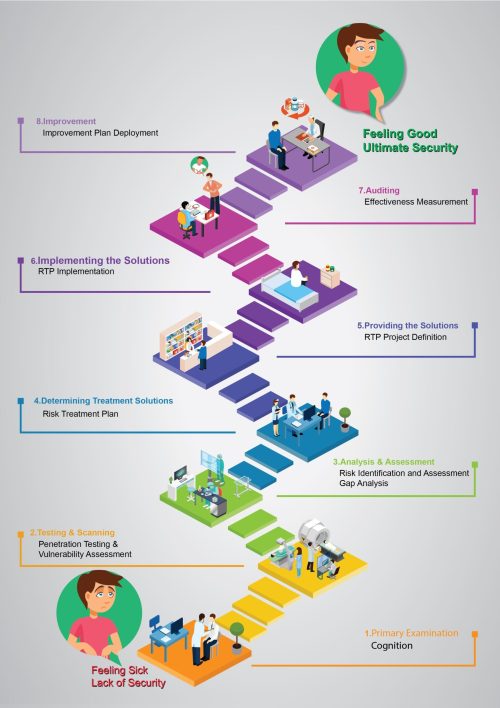
Our model is a multi-layered, end-to-end framework based on PPDIOO (Prepare, Plan, Design, Implement, Operate, Optimize), aligned with the Deming Cycle, and covering all approaches to information security management. It consists of 1 primary stage (2 phases, 7 steps) and 4 main stages (6 phases, 20 steps). Each step contains key activities to ensure practical, measurable results.
Many CEOs and CISOs believe their organization is already “secure enough.” But in today’s threat landscape, hidden vulnerabilities can exist even in mature environments — often without being noticed until it’s too late.
Before investing in a full security program, you need clarity:
Do you really need to strengthen your security posture? How exposed is your business today?
Stage 0 is designed to give you clear, objective answers.
Using our Security Posture Self-Assessment Toolkit, you will:
Reveal hidden security gaps that could put your business at risk
Understand your true level of protection, not just perceived security
Evaluate the potential financial and operational impact of unresolved vulnerabilities
Determine how urgent security improvements are for your organization
This stage provides practical insights and measurable results, helping you make confident, informed decisions about your security strategy — before risks turn into incidents.
Know your exposure. Understand your risk. Take action with confidence.
Executive Security Posture Assessment: Evaluate current security status across domains.
Total Loss Estimator: Estimate potential financial losses from security gaps.
Implementation Urgency: Assess urgency and prioritize improvements
Project Definition: Define high-level objectives and alignment with business priorities.
Boundary Definition: Determine project scope and limits.
Security Domains Posture Assessment: Evaluate in-depth status of targeted security domains.
Readiness Assessment: Confirm organization’s readiness to undertake ISMS implementation.
If your assessment reveals opportunities to strengthen your security posture — or identifies gaps across critical domains — now is the time to take action.
Security is not a one-time effort, but a continuous journey toward resilience, trust, and business protection. By moving forward, you take control of your risks, reduce potential losses, and build a stronger, more secure organization.
Together, we will:
Prioritize the areas that need improvement
Strengthen your security across key domains
Implement practical and effective protections
Guide your organization toward a mature and resilient security posture
Your journey to stronger security starts here. Let’s move forward with confidence.
Assess readiness, challenges, and information availability.
Map organizational structure, goals, strategies, and obligations.
Identify all assets (information, hardware, software, human resources, infrastructure, intangible).
Document, map, and analyze all business processes.
Allocate resources, define tasks, timing, and deliverables.
Determine project scope, stakeholders, and interdependencies.
Identify gaps between current and target security states.
Quantify asset value and role in achieving business goals
Identify, analyze, and evaluate risks to assets.
Define solutions and mitigation plans for unacceptable risks.
Develop long-term strategy and objectives.
Establish policies, procedures, and technical guidelines.
Define role-based training and awareness programs.
Identify critical services, recovery objectives, and DR strategy.
Plan rollout of technical and organizational controls.
Oversee execution and ensure compliance with strategic plan
Maintain security controls, monitor performance, and respond to incidents.
Evaluate compliance, performance, and effectiveness.
Review metrics, incidents, and lessons learned.
Implement corrective actions and optimize security posture.
Ultimate Security covers everything in information security, including:
And much more …
ISO/IEC 27000 Family
Other ISO/IEC Related Standards
NIST Standards
Security Standards for Industries
Power Industry
Financial Systems
Healthcare
Risk Management Frameworks
Program & Governance Frameworks
Control Frameworks
Compliance & Privacy Frameworks
Identity & Access Management Frameworks
Incident Response Frameworks
Foundational Principles & Philosophy
Program Planning & Documentation Guidance
People & Process Operation Guidance
Technical Implementation Guidance
Measurement, Assessment & Governance Guidance
Sector / Domain Guidance
This model is:
Who Benefits
Move from security as a cost center to security as a business enabler. Our methodology provides the roadmap, tools, and framework to achieve information security excellence while optimizing your resource investment.
If you are about to implement an ISMS or any Information Security Enhancement project to improve your current information security posture, request us a technical and financial proposal: