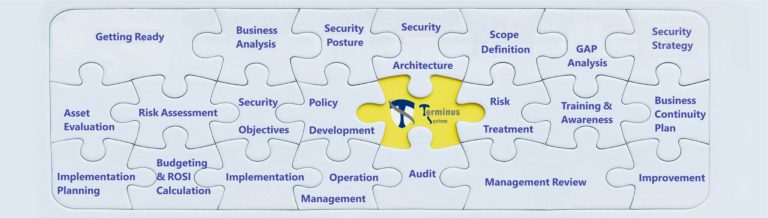
All-in-one Information Security Platform
“Enhance your organization’s security stance, safeguard your assets, synchronize security with your business objectives, and proactively mitigate potential threats with our sophisticated and economical All-in-one Information Security Platform”
Experience a new standard in security excellence with our comprehensive suite of features
- Comprehensive and Agile Security Evaluation
- Holistic Security Assessment
- Innovative Security Architecture Design
- Smart Asset Evaluation
- Strategic Security Planning Aligned with Business Objectives
- Advanced Risk Assessment
- Customized Risk Management Planning
- Compliance Assessment & Gap Analysis utilizing diverse security maturity models
- ROI Calculation for Security Investments
- Intelligent Training and Awareness Program Planning
- Business Continuity and Disaster Recovery Planning
- Efficient ISMS Implementation Management
- Thorough Audit Processes
- Assessment of Implementation Effectiveness
- Security Posture Assessment
- Tailored Recommendations for Optimal Security Boundaries
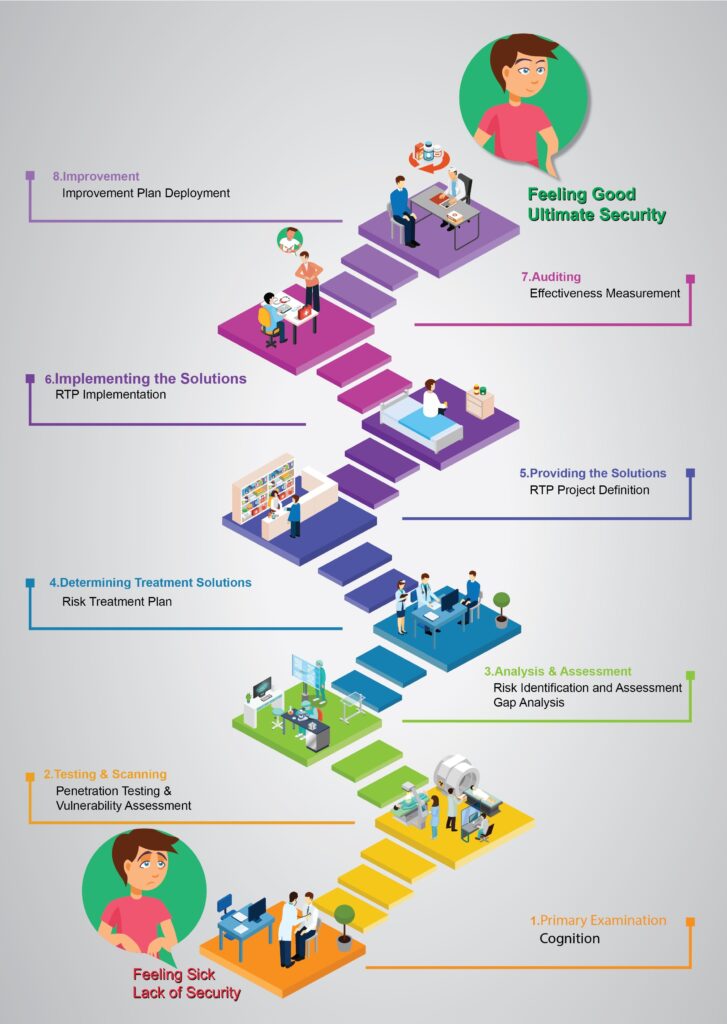
The structure of this unique methodology is based on the PPDIOO (Prepare, Plan, Design, Implement, Operate, Optimize) model, corresponds to the Deming Cycle, and covers all five above-mentioned approaches. It has a multi-layer structure with 21 steps:
Guarantee your compliance to



Your Customized Policy


C2M2
NIST SP 800-53
CIS
CMM
ISM3
ISO27017
ISO27031
ISO22301
ISO 27031
GRC
FCRA
ISO27005
Experience the ultimate security at an incredible price with us
Model Straucture
Prepare
The Prepare phase in this methodology, is the initial stage in the process of design and deployment. During this phase, an organization gets ready to start a successful implementation of the ISMS project. The Prepare phase is critical as it provides the basic requirements to start the project. During this phase, essential information and requirements to understand the organization’s goals and constraints will be gathered.
The primary objective of this step entails assessing the readiness to commence the ISMS project, identifying potential challenges, resolving them, and determining the whereabouts of necessary information throughout subsequent steps and phases. In other words, this step shows if organization is ready and capable of moving forward with the project. The activities of this step are:
- Readiness Assessment
Evaluating whether the organization is prepared to undertake the ISMS project, including resource availability, management support, level of culture and security maturity, organizational structure and existing security practices.
- Challenge Treatment
The purpose of this activity is to resolve implementation challenges and guarantee the success of the project. The main possible challenges are:
- Challenges caused by wrong assumptions and paradigms
- Challenges arising from the implementation environment
- Emerging challenges in the processes
- Challenges arising from project management and technology
- Information Containers’ Inventory
Determining where necessary information can be found, which is essential for the subsequent steps of the ISMS project.
The purpose of this step is to get information about different organization’s structures. The process of recognition can be done through interviewing and reviewing the documentation. The main activities of this step are:
- Organization Structure
The required information for this activity is as follows:- List of personnel
- Organization’s units
- Top chart of the organization
- Job roles
- Interested Parties
The required information for this activity is as follows:- List of interested parties
- Their requirements & expectations
- Business Goals & Objectives
The required information for this activity is as follows:
- Business Goals or BSC
- Business Objectives in SMART format
- Business Strategy
The required information for this activity is as follows:
- Vision
- Mission
- Strategy
- History
- Jobs Information
The required information for this activity is as follows:
- Job roles
- Required competency
- Business Problems
The required information for this activity is as follows:
- List of problems
- Products & Services
The required information for this activity is as follows:
- List of products / services
- Training Records
The required information for this activity is as follows:
- Training records of personnel
- Obligations
The required information for this activity is as follows:
- Details of all security related obligations
- Environment Analysis
The required information for this activity is as follows:
- Internal environment analysis
- External environment analysis
The purpose of this step is to prepare a list of all assets and their characteristics and properties.
Assets can be divided into main categories of the Safe Area such as data centers, Hardware such as switches, Software such as applications, Information such as files and documents, Human resource such as personnel, Storage such as CD, Infrastructure such as LAN and Intangible such as patents.
- Information
In this classification, information assets are divided into the following two categories:
- Digital Files such as CAD files
- Paper Documents such as Paper Letters
- Software
In this classification, software assets include all software except electronic files. Some examples of software assets are:
- Web Applications
- Operating Systems
- Databases
- Infrastructure
- Networks such as LAN, WAN
- Cloud Environment
- Emergency Power System
- Storage
In this classification, storage assets are all portable and removable assets. Therefore, storages installed on hosts such as RAM and Hard Disk are not included. Some examples of storage assets are:- External HDD
- CD/DVD
- Flash Memory
- Hardware
The meaning of Hardware asset in this classification is the following items and does not include hardware used in infrastructures like switches or UPS and portable storages:
- Hosts such as Computers, Servers
- Office Appliances such as Printer
- Office Supplies such as Video Projector
- Human Resource
- Personnel
- Contractor
- Supplier
- Safe Area
- Data Center
- Server Room
- Power Room
- Intangible
- Patents
- Trademarks
- Copyrights
The purpose of this step is to define business processes based on relevant standards. Activities of this step are:
- List of Processes
In this activity list of all business processes including Main, Supportive, Management process will be provided.
- Process Mapping
In this activity, the relationship between each process with the goals and products resulting from the implementation of that process is determined.
- Process Documentation
For each process the following information is required:
- Type (Main, Management, Supportive)
- Related goals
- Input
- Sources
- Output
- Destinations
- Quality indicators
- Responsible (for design, presentation, maintenance, monitoring, management, support), Accountant, Consultants, Informed
- Involved assets
Plan
After getting prepared for ISMS design and implementation, it is time to Plan for it. During this phase, essential information and requirements to understand the existing security posture will be gathered. The Plan phase is critical as it sets security architecture, defines the boundary of project, determines the gap and evaluates the assets.
The aim of this step is to evaluate the current security posture, establish the objectives of ISMS implementation, and develop a roadmap for transitioning from the current state to achieve the defined goals.
- Primary Assessment
Security posture denotes an organization’s comprehensive security position or preparedness to safeguard its assets, data, and information systems against potential threats, attacks, and vulnerabilities. The objective of this activity is to gather information regarding the following items:
- Current security status
- Project goals
- Project boundary
- Project Plan Development
This activity includes the following two steps:
- Technical & Financial plan development
- Project Management plan development
The security architecture design encompasses the strategic framework for safeguarding an organization’s assets, data, and information systems. It begins with defining the security organization, delineating roles, responsibilities, and reporting structures to ensure clear accountability. Setting standards involves establishing guidelines and protocols governing security practices, frameworks provide comprehensive structures for implementing security controls and risk management processes and relevant laws and regulations ensures legal adherence and protection of sensitive information, considering laws. This holistic approach ensures a robust security architecture capable of mitigating risks and supporting the organization’s objectives securely.
- Security Organization
The purpose of this activity is to formulate the optimal organization information security structure. At this step, the organization’s existing information security structures and their components, and the job description of each one identified in the recognition phase, were identified with a desirable structure in which all the security responsibilities of an organization in four levels of management, strategic, operational and, monitoring & maintenance, and support are defined and assigned to an ideal structure, then the weaknesses of this structure are determined and the desired structure is proposed.
- Security Standards
Some security standards that this model covers them are:
- ISO27001
- ISO27005
- ISO27032
- ISO22301
- Security Laws & Frameworks
Some security laws and frameworks that this model covers them are:
- COSO
- GDPR
- GRC
- SOC2
- HIPPA
- PCIDSS
- NIST
- Security Maturity Models
Some maturity models that this model covers them are:
- ISM3
- C2M2
- NIST CSF
- CEM
- CIS
- SANS CSC
At this step, which is one of the most important and crucial parts of the definition of the Information Security Management System, the scope of the project is determined. The purpose of this step is to accurately define the scope of the project based on the indicators defined in ISO27001. In accordance with Clause 4.2 of ISO27001, the scope definition indices are:
- Internal and external risks towards the realizing goals of information security by recognizing the organization and the external and internal context.
- Identifying the stakeholders of the information security management system and their needs and expectations of the system.
- Identify interfaces and interdependencies between activities of the organization and other organizations
The only activity of this step is:
- Internal – External Issues
In order to analyze the internal and external environment, ISO31000 as an appropriate reference is used.
Analyzing the gap between current situation and the ideal situation in designing a roadmap has a significant impact. In the ISO 27001 controls gap analysis section, the quality of the implementation of ISO / IEC 27001 controls is carefully assessed based on the criteria in ISO / IEC 27002, and by specifying the CMMI model, the maturity level of each control is separately determined and each control is examined in terms of design, implementation, review and improvement status, and ultimately will be in one of the sub-primary, primary, planned, defined, controlled, optimized levels of maturity. The purpose of this step is to formulate a Statement Of Applicability.
Also, the maturity level of each selected framework, law or maturity model is separately determined.
At this step, assets should be evaluated. A common method in this regard is the question of the owner of a property that is not very accurate and is not recommended by different standards. Based on the standard, the evaluation indicators should be chosen in such a way that they can be compared to different results at different times and by different people, while the conventional approach will certainly differ from those of the different people according to their relationship to the asset.
The method presented in this model is based on the role of each asset in achieving the goals of the organization, thus covering all standard features. To this end, the goals of the organization are first weighted. For this purpose, various methods such as AHP can be used. It is the time to rate the processes. Each process is valued based on the amount of impact it has on each objective, taking into account the target weight of the target. For each process, four indicators are which are presented at an acceptable time, maintaining the confidentiality of the data, maintaining the authenticity of data and quality, and for each index separately evaluated and ultimately the value of each process is calculated. The value of each asset is now determined by the role of each asset in each process, taking into account the value of that process. For this purpose, the types of assets involved must be identified for each business process.
The activities of this step are:
- Goals Weighing
- Process Weighing
- Asset Impact Assessment
- Financial Value of Assets
- Asset Evaluation
Design
This phase is the basis for information security management system implementation and is critical as it sets the direction and framework for the entire deployment process, ensuring that the solution aligns with the organization’s needs and goals
After identifying assets and evaluating them, identifying the risks to them is a necessary part of the implementation of ISMS. Recognizing the risks to different assets and determining the probability of occurrence of each one and the extent of the damage and consequences in the event of occurrence and, finally, the quantitative and qualitative calculation of the amount of risk is the goal of this step. At this step, a list of risks is first provided for each type of asset. After identifying the risks of each asset, identifying the security threats that may lead to its occurrence is done. Ultimately, the vulnerabilities if each asset is identified. To identify risks and threats, one can use interviews with audiences and review are known risks. Also, upstream and downstream requirements and stakeholders’ needs are other sources for identifying risks. Ultimately, the vulnerabilities and weaknesses of the various assets that could lead to the occurrence of threat should be identified. The components of this step are:
- Risk Identification
There are various events that can affect an asset and consequently “take on a risk.” Identifying the reasons that can endanger the security of the asset, the place where these factors can be problematic and how it is determined and how it is identified. There are many ways and means to define the risks and the reasons for their occurrence, including the checklist, a judgment based on experience and records, flowcharts, collaborative sessions, system analysis, analysis of different scenarios and engineering techniques of the systems. To determine the appropriate method of risk assessment, the following techniques can be considered:
- Brian storming sessions
- Structured methods such as flowcharts, review of system design, system analysis, hazard studies
- Use the experiences of others and prepared tables
- Threat Intelligence
After identifying different risks, for each risk, the threats that can lead to that risk should be identified. Its origin can be used to fully identify the threats. Threats can be categorized as:
- Occurrence: Usually occurs without planning and accidental incidents such as natural disasters or equipment failure
- Intentional: Deliberately and with prior planning like sabotage
From another point of view, it can be classified as follows:
- Active: If successful, it changes in assets.
- Inactive: If successful, it does not change the asset, such as eavesdropping.
Any threat to carry out its sabotage requires motivation. Threat motives can be one of these:
- Financial: It takes to earn money or financial benefits.
- Opportunistic: Opportunity if available.
- Business: It is for the benefit of commercial interests.
- Belief: It is for personal belief or for political or personal reasons.
- Ability: It is done to show the ability to perform.
- Identification of Vulnerabilities
In this section, the vulnerability of each group of assets is identified using automated tools and security scans or interviews or observations.
- Risk Evaluation
In this section, for each risk, records of the occurrence and the amount of control and countermeasures against it are reviewed. In risk assessment for each risk, the probability of occurrence and its consequences should be calculated. Generally, the risks can be divided into two main categories of incidents and cybercrime & vandalism. The first step is to calculate the number and degree of vulnerability for each risk. By identifying the vulnerabilities in each asset and the relationship between each vulnerability with each risk, the severity of the risk is calculated. After that, the probability of occurrence and consequences should be calculated. Also, the number of asset vulnerabilities for a particular risk, previously defined as the vulnerability level, is considered, and the probability of occurrence is calculated by combining these three factors: the rate of occurrence, the amount of coping before damage and the degree of vulnerability. To calculate the extent of the consequences of each risk, two factors influence the risk effect on each security index of each asset and its security index value.
The indicators used to calculate the probability of occurrence of cybercrime and sabotage risks include:
- Attack method (internal-external) from inside or outside of the organization
- The complexity of the attack (high-low) based on the CVE number of the vulnerability
- Authentication (requires – does not need)
- Attack tool (not available – Hardly accessible – Available – No tools needed)
- Implemented Countermeasures (the definitive strategy applied – the temporary solution implemented – is in place – no solution)
- Creating Risk Matrix
Now for each risk, based on the probability of occurrence and degree of impact, the risk level and its position in the risk matrix are determined. The risk number is the probability of occurrence of a risk multiplied by its impact.
The security strategic plan outlines the overarching framework for safeguarding an organization’s assets and information systems. It begins with defining clear security goals aligned with business objectives, establishing measurable security objectives to guide implementation efforts. In order to measure the success rate in the implementation of the information security management system, the objectives and the method of measuring it should be determined. In fact, the effectiveness of this system and the concept of security, which is an intangible concept, can be measured. For this purpose, different indexes such as risk number, and maturity levels are used.
Setting a risk acceptance level helps determine the threshold for tolerable risk exposure, informing decision-making processes regarding risk mitigation strategies. The security strategy encompasses a comprehensive approach to risk management, including preventive, detective, and corrective measures, as well as incident response protocols, security awareness training, and continuous monitoring to ensure proactive threat mitigation and alignment with the organization’s risk appetite and operational needs.
Activities of this step are:
- Setting Security Goals and Objectives
- Setting Risk Acceptance Level
- Security Strategy Development
The purpose of this step is to develop the statement of the information security policy, technical policies & procedures for policy implementation.
- Security Policy Development
Information Security Policy is a high-level document that describes security requirements.
- Security Technical Policies Development
In this step, security policies are being developed to provide a systemic response to security risks. The technical security policies are in fact systems management solutions for threats, and their content should result from risk analysis and statement of applicability. Policies are the first level of system documentation that their initial list is based on the recognition and the requirements presented in the standard text and the results of the risk analysis and statement of applicability. Information Security Policies are based on the following two types:
- Subject-based security policies
- System-based security policies
- Security Procedures Development
Security procedures are defined for enforcing security policies. A procedure defines mechanisms for security regulation. Based on the technical security policies and requirements in the standard text and the results of the risk analysis and the statement of applicability, a draft of the procedures is prepared and reviewed at the meetings with the relevant authorities.
The purpose of this step is to provide solutions to address the identified risks. Based on the acceptable level of risk, a solution and security plan is provided to manage risks that are beyond acceptable levels. Major tasks of this step are, developing risk management plan, determination the effectiveness of the solutions based on defined indicators, and the determination of the extent to which the objectives are achieved in the event of full implementation of the plan.
- RTP Development
Risk Treatment Plan can be divided into technical and systemic solutions. The technical solutions includes a variety of hardware, software, and configurations, and policies, procedures, and training courses are in the systemic solutions. In this activity, appropriate solutions are determined and for each solution, the implementation method, the type of solution’s impact on the security parameters, the type of solution and the related risks will be determined. The followings are determined for each solution:
- Implementation method which are Hardware, Software, Configuration, Procedure, Training, Awareness
- The impact of the solution on the security index which is Confidentiality, Integrity, Availability
- Type of solution which is Preventive, Diagnostic, Reaction, Recovery
- Related threats
- RTP Effectiveness Assessment
Now that the list of solutions has been extracted, the impact of each solution is determined. For this purpose, the following are calculated for each solution and for all threats:
- Number of covering vulnerabilities,
- Risk number reduction
Definition of the required training and awareness programs are the output of this step. One of the factors that play an effective role in creating and maintaining information security is the awareness of the personnel about their rights, duties, responsibilities regarding the organization’s information security program. In order to develop proper training courses, each person’s role in the information security structure and the description of the respective security duties are considered, the training courses required by each individual to provide an optimal description of the services is identified and by considering the training records of the person his training calendar will be generated. This training calendar is tailor-made by an intelligent and targeted manner. Activities of this step are:
- Training Plan Development
- Awareness Plan Development
In the organization’s information security structure, a plan for managing the accidents including the definition of the duties and responsibilities of each person in different situations should be provided. In this step, while identifying key services, their importance for the organization and the definition of crisis situations and RTO, RPO for the key services are calculated.
- Business Continuity & Disaster Recovery Plan Development
The general components of a business continuity plan are:
- Recognition: Identifying key services by assessing the impact of each service deficiencies on the organization’s activities is the first part of this step. After identifying key services, RTO and RPO are calculated for each key service.
- Strategy development: All possible options and strategies for continuity and return of any key services after failure should be identified and documented.
- Test: The scope and risks of testing, should be documented and verified by the management. In conducting the tests, all involved in coping with the crisis must have at least one of the tests, and all three test methods (simulation, parallelism and complete stop) must be used.
Implement
The “Implement” phase involves the actual deployment of the security design that was developed during the earlier phases (Prepare, Plan, and Design). This phase is where the planned changes and configurations are put into action to create the desired level of security. The Implement phase is focused on executing the planned changes and configurations to build the security infrastructure according to the design specifications developed in earlier phases, while also ensuring minimal disruption to existing operations.
The goal of this step is to plan for risk treatment solutions implementation. In this step, implementation of the solutions presented in the design phase will be considered.
- Implementation Plan Development
This activity covers the plans for:
- Procurement and installation of hardware and software
- Configuration of devices
- Testing and validation
- Training
- Policy implementation
- Change management
- Budgeting & ROSI Calculation
The budgeting for the plan consists of:
- Cost Estimation
- Prioritize Spending
- Contingency Planning
- Lifecycle Costs
ROSI calculation consists of:
- Identify Benefits
- Quantify Benefits
- Calculate Costs
- ROI Calculation
- Consider Risk Reduction
- Sensitivity Analysis
In this step, the project management plan for the approved projects for implemenatation is developed.
- Implementation Project Management Plan Development
- Procurement and installation
- Configuration
- Testing and validation
- Training
- Policy implementation
- Change management
Operate
The “Operate” phase involves the actual management and operation of the Security Solutions that has already been designed and implemented. This phase focuses on the day-to-day security operation activities. The Operate phase is focused on ensuring the required level of security, and performance of the infrastructures to meet the needs of users and applications effectively.
The goal of this step is to operate risk treatment plan based on implementation planning and management steps.
Key activities of this step are:
- Monitoring
- Troubleshooting and problem resolution
- Configuration management
- Performance optimization
- Capacity planning
Optimize
In the last phase, the security situation after operating the RTP will be analyzed and all remaining issues observed are removed and the final corrections in the system are considered. This phase includes Audit, Review and Improvement.
In this step, effectiveness of implemented solutions is measured and has two activities:
- Effectiveness Assessment
In this activity, the effectiveness of the implemented solutions is measured. In fact, by assessing the organization’s information security status before and after the implementation, the effectiveness of the implementation of the information security management system is measured and compared with the goals set. The followings in this activity are measured:
- Controls Gap Improvement Assessment
- Effectiveness Assessment
- Risk Level Improvement Assessment
- Security Maturity Improvement Assessment
- Internal Audit
In this activity, an internal audit and also security audit is performed to assess the quality and standardization of the implementation of standard solutions.
In this step, the design is subject to review in accordance with the results of the effectiveness assessment and internal audit. After an internal audit and assessment of effectiveness, if the intended security objectives are not met, the necessary corrective actions are defined to achieve the objectives and are approved at the management review meeting. In accordance with the approvals of the management review and, if necessary, the technical documentation provided, in particular, the risk management plan, is revised. Activities of this step are:
- Management Review
- Corrective Actions Plan
In this step, corrective plans to improve the information security situation will be implemented. This step is very similar to the implementation, except that only corrective actions are performed. The three main activities of this step are the implementation of corrective plans resulting from the review phase, reassessment of the goals achieved after corrective actions, and finally informing stakeholders about the improvements.
- Corrective Actions Implementation
- Reassessment of achieved goals
- Informing stakeholders about the improvements
Frequently Asked Questions
Yes, it provides a toolkit to assess your current security posture from various perspectives and evaluates the urgency of any necessary improvements.
By utilizing this platform, you can define your security goals aligned with your business objectives and the necessity of ISMS implementation
Yes, based on your business goals and requirements, it defines the boundary very precisely.
Yes, this platform effectively aligns security with the strategic objectives and business goals of your organization. It supports your overarching mission while addressing specific security requirements and priorities.
Yes, it offers flexibility to accommodate the unique needs, size, and complexity of your organization. It is adaptable to various industries, regulatory environments, and organizational structures, allowing for customization as necessary.
Yes, it provides comprehensive coverage of all relevant aspects of information security, including risk assessment, policy development, controls implementation, training, auditing, compliance, and continual improvement processes.
Yes, it offers clear documentation, guidelines, templates, and tools to support each phase of the implementation process. Clear guidance facilitates consistency, reduces ambiguity, and streamlines the implementation effort
Yes, it emphasizes measurable outcomes and continuous improvement. It includes mechanisms for monitoring progress, measuring performance against predefined objectives and targets, and implementing corrective actions as needed to enhance the effectiveness of the ISMS over time.
